Blockchain technology has revolutionized the way we store and share information online. However, with the increasing use of digital information (Cryptography and Blockchain Technology), the security and privacy of data have become more important than ever.
To ensure that information is kept secure and private, blockchain technology has made cryptography an essential component. It uses complex mathematical algorithms to protect data and ensure that it is tamper-proof.
The concept of cryptography has been around for centuries, but it is only in recent years that it has become a critical aspect of the digital world. It has become increasingly important as we move towards a more digitalized society, and its use has expanded to include blockchain technology.
In this blog, we will explore the concept of cryptography in the blockchain world. In addition, we’ll look at how cryptography is used to keep data secure and why it is an essential component of the blockchain ecosystem.
Cryptography and Blockchain Technology: Unlocking the Secrets of Cryptography?
In a nutshell, cryptography is the science of hiding data. More specifically, modern cryptography employs mathematical theories and computation to encrypt and decrypt data. This helps to ensure the integrity and authenticity of the information.
In a basic text encryption process, plaintext (data that can be plainly understood) is encrypted, resulting in ciphertext (which is unreadable). By doing so, one can ensure that the information transmitted can only be viewed by someone who has a certain decryption key.
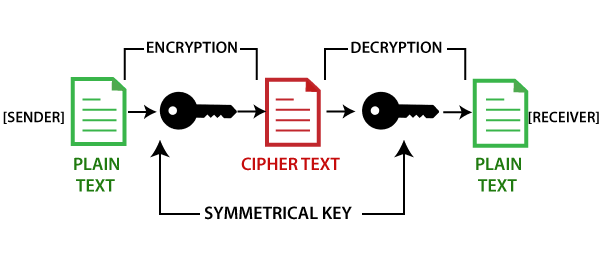
By employing specialized encryption algorithms, it is possible to communicate sensitive data via unsecured networks. The level of encryption will be determined by the level of protection required for the data. For example, the kind of security used on regular personal files (such as contacts) differs from that utilized on cryptocurrency networks.
This indicates that understanding the importance of cryptography inside cryptocurrency or blockchain systems requires a grasp of how it works. Most blockchain systems, such as Bitcoin, employ a specific set of cryptographic protocols. This enables them to serve as a decentralized and public ledger. Through which digital transactions can be conducted in a highly secure manner.
Apart from that, it involves techniques like symmetric and asymmetric encryption, as well as hash functions, to protect the confidentiality, integrity, and authenticity of the information.
Symmetric & Asymmetric Encryptions in Cryptography
Symmetric encryption is a type of encryption where the same key is used for both encryption and decryption. This means that the sender and the receiver of a message share the same secret key.
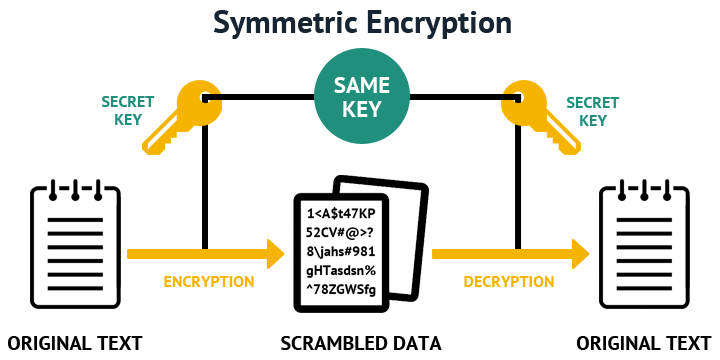
One of the main benefits of symmetric encryption is that it is computationally efficient. The encryption and decryption processes are relatively fast and require minimal processing power.
However, one of the main drawbacks of symmetric encryption is that it requires a secure method of sharing the secret key between the sender and receiver. If the key falls into the wrong hands, an attacker could easily decrypt the ciphertext and gain access to the original plaintext message.
Asymmetric encryption, also known as public-key encryption, is a type of encryption where two different keys are used for encryption and decryption. The keys are mathematically related, but it is computationally infeasible to derive the private key from the public key.
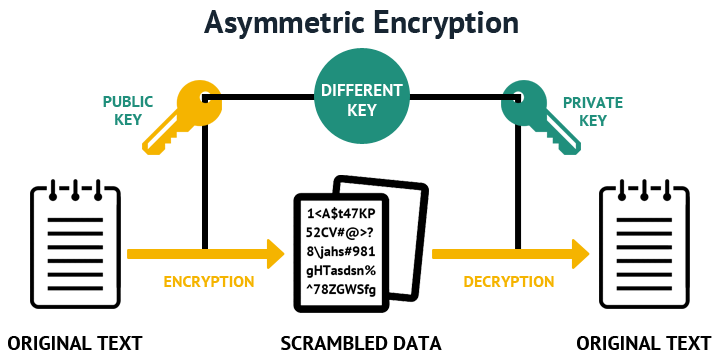
In this process, the receiver generates a public-private key pair. The public key is shared with the sender, who uses it to encrypt the plaintext message. This means that the sender does not need to share their secret key with the receiver, providing a higher level of security.
One of the main benefits of asymmetric encryption is that it provides a higher level of security than symmetric encryption. As it does not require the exchange of a secret key. But one of the main drawbacks of this process is that the encryption and decryption processes are much slower than those of symmetric encryption. And require significantly more processing power.
Apart from that, Hash Functions are another way cryptography may secure information. Instead of keys, it employs algorithms to convert any data input into a fixed-length string of characters.
How Blockchain Technology Leverages Cryptography to Safeguard Data
Blockchain technology uses several cryptographic techniques to ensure the security and privacy of its transactions. Here are some of the key ways that blockchain technology is utilizing cryptography:
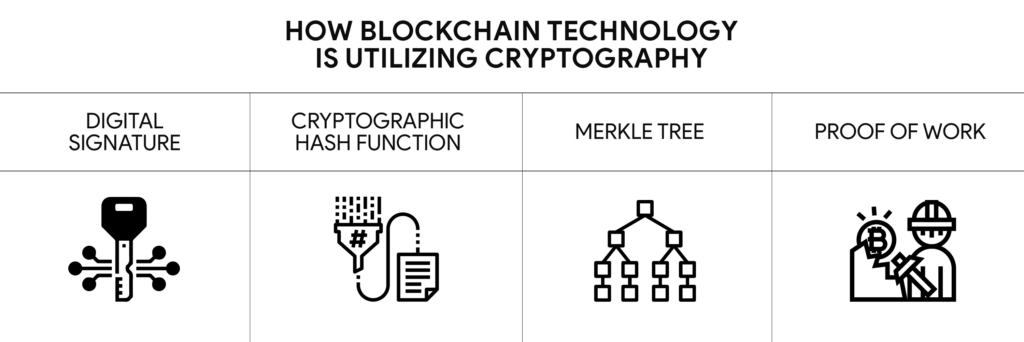
- Digital Signatures: Digital signatures are cryptographic techniques used in blockchain technology. A digital signature is a mathematical algorithm used to verify the authenticity of a transaction.
When a participant sends a transaction, they sign it using their private key, which creates a digital signature. The recipient can then use the sender’s public key to verify the digital signature. And ensure that the transaction is authentic.
- Cryptographic Hash Functions: These are mathematical algorithms used to ensure the integrity of data on the blockchain. When a transaction is added to the blockchain, it is hashed using a cryptographic hash function. The resulting hash value is unique to the transaction and acts as a digital fingerprint.
Any modification to the transaction could easily be detected by a different hash value. This feature ensures that no one can modify transactions on the blockchain without being detected.
- Merkle Trees: Merkle trees are a data structure used to ensure the integrity of large amounts of data on the blockchain. A Merkle tree is created by hashing groups of transactions together. And then hashing those hash values together to obtain a single root hash value.
- Proof of Work: It is a consensus algorithm used in some blockchain networks, such as Bitcoin. In PoW, participants must solve a complex mathematical puzzle to add a block to the blockchain. This helps to ensure the security of the blockchain by preventing malicious actors from adding fraudulent blocks to the blockchain.
In short, blockchain technology utilizes several cryptographic techniques to ensure the security and privacy of its transactions.
Drawbacks of Using Cryptography
Before implementing cryptography in blockchain technology, we need to consider its drawbacks. These drawbacks include complexity, performance, and cost.
- Complexity: Cryptography is a complex process that requires expertise to implement and maintain. The implementation of cryptography requires knowledge of complex mathematical algorithms, which can be challenging for developers who are not familiar with the technology.
- Performance: The use of cryptography can slow down the performance of the blockchain network. The encryption and decryption processes require significant computational resources, which can slow down the speed of the network. The more complex the cryptography, the slower the network becomes.
- Cost: The implementation of cryptography can be expensive, as it requires specialized hardware and software. The cost of hardware and software required to implement cryptography can be a significant barrier to entry for small organizations or individual developers.
- Quantum Computing Threat: Cryptography algorithms used in blockchain technology may become obsolete with the advent of quantum computing, which can solve complex mathematical problems faster than traditional computers. Quantum computers could potentially break the encryption used in blockchain technology, rendering the blockchain vulnerable to attacks.
This indicates that cryptography might play a crucial role in securing the data stored on the blockchain. However, it is important to consider the drawbacks associated with its implementation.
Conclusion
Cryptography is a crucial element in ensuring the integrity and security of blockchain technology. This can keep the data stored on the blockchain confidential and tamper-proof.
Meanwhile, cryptography may have some drawbacks, but its benefits far outweigh them in terms of data protection and verification. As blockchain technology continues to grow and evolve, the importance of cryptography in maintaining its security will only continue to increase.
To know more about the link between Cryptography and Blockchain Technology, go check out SunCrypto Academy.