With the growing popularity and value of cryptocurrencies, there has been an increase in crypto scams, and mobile devices are no exception. These crypto scams take numerous shapes, but they all have the same goal: to steal your hard-earned cryptocurrency.
The following article will discuss several mobile device crypto scams and show you how to secure your device from them. Let us start!
What are Mobile Devices Crypto Scams?
According to Statista, the number of smartphone users currently stands at 6.93 billion, which means that 86.34% of the world’s population has a smartphone (via phone numbers). As a result, mobile device scams are any scam that targets victims using a mobile phone or other mobile device. They can take the form of detrimental apps, text messages, websites, or phone calls.
Some mobile device crypto scams attempt to fool you into providing personal information, such as your cryptocurrency exchange account or wallet keys. Others will attempt to get you to install malicious software on your device. Some will even attempt to deceive you into sending them cryptocurrency.
Avoiding mobile phone fraud has become an active part of our lives, especially when new tactics to deceive people emerge on a daily basis. However, certain crypto scams are not always evident, so knowing how to recognize one is vital for protecting yourself.
Different Types of Crypto Scams on Mobile Devices
Today, mobile phones are nearly considered extensions of our bodies, and hackers are well aware of this. We always carry our mobile devices with us, and we use them to access everything from kitten videos to our most personal information. We’ve linked bank and cryptocurrency exchange accounts, emails, and other sensitive data to our phones, making them prime targets for cryptocurrency theft and fraud.
There are many various sorts of mobile device scams that could harm your crypto exchange accounts or wallets. Some of the most notable ones are:
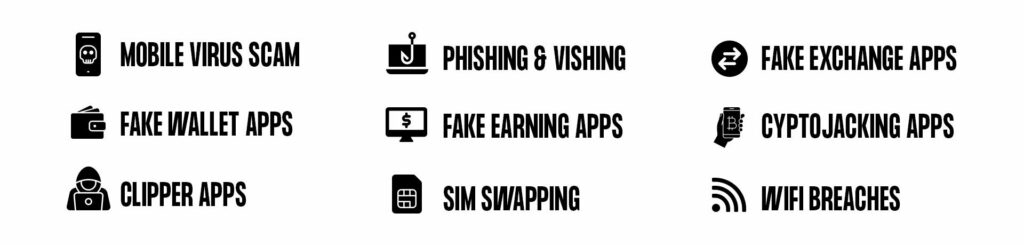
▪️ Mobile Virus Scams: A mobile virus is a sort of malware that can infect your mobile device in the same way that a computer virus does. While browsing specific websites on your phone, you may have noticed a message informing you that a scan of your phone discovered a virus infection and urged you to download an antivirus app right now.
However, this program is malware or spyware that attempts to infect other devices or hijack your own. This might give scammers access to all of your passwords and accounts, including cryptocurrency exchange accounts and wallets. The simplest approach to defend yourself from these kinds of attacks is to ignore any browser pop-ups while also keeping cybersecurity on your phone.
▪️ Phishing & Vishing: Phishing is a type of scam in which an attacker impersonates a legitimate website, app, or service in order to fool you into providing your personal information. They accomplish this by developing a bogus login page that appears identical to the real thing. Phishing scams are among the most popular crypto scams nowadays.

Phishing scams are also carried out via SMS texts, which are referred to as “smishing.” These types of crypto scams attempt to get you to click on the malware URLs received by SMS. If you click the link, your device will become infected with malware or spyware.
Vishing is similar to phishing, except that instead of utilizing a phony website, the attacker will attempt to mislead you with a false phone call or text message. These types of crypto scams are growing increasingly common, and they can be difficult to detect.
The easiest approach to protect yourself from phishing scams is to use only approved websites and bookmark those that contain critical information so you can quickly access them. When it comes to vishing attacks, the key is to never provide personal information, even if the person or website appears real.
▪️ Fake Exchange Apps: Fake exchange apps are exactly what they sound like – mobile apps that scam crypto investors into thinking they are the real ones. The most well-known example of such a cryptocurrency exchange app is most likely the one of Poloniex.
Prior to Poloniex’s launch of their official mobile trading app in 2018, Google Play was already listing several fake exchange apps with the same name. Many users who downloaded the fraudulent apps tried to log in, thus basically handing over their Poloniex crypto account login credentials to the scammers. It goes without saying that their crypto holdings on the exchange were wiped out. Some other apps went even further requesting the login credentials of users’ Gmail accounts.
When it comes to protecting your cryptocurrency investments from such crypto scams, you can do numerous things, including:
1️⃣ Use two-factor authentication (2FA): It is crucial to note that in our case above, crypto was stolen only from accounts that did not have 2FA enabled. While 2FA is not impregnable, it is very useful because scammers will have a difficult time defeating it even if they have your exchange login information.
2️⃣ Check the veracity of the program you’re downloading by looking at the number of downloads, reviews, and ratings; phony apps feature either comments where people complain about being cheated or immaculate scores.
Furthermore, legitimate programs are made by legitimate firms, and you may get information about the developers on the app store. You might also visit the official exchange website and see if the software they are selling is the same as the one available in the mobile app store.
▪️ Fake Earning Apps: Another type of fraudulent cryptocurrency mobile app is the so-called earning app. The theory behind these apps is that they usually provide users with a method to earn cryptocurrencies by completing specific tasks. These apps typically advertise themselves as freebies or phony high-yield earning apps.
In truth, most of these earning apps are crypto scams designed to take people’s cryptocurrency. To prevent getting duped by a bogus earning app, look for any red flags, such as large payouts for no work. You can also examine the app’s legitimacy by looking at its ratings, developers, and so on.
▪️ Cryptojacking Apps: Cryptojacking apps are another type of risky cryptocurrency app that we’ll discuss. Cryptojacking is an attack in which the attacker utilizes your device to mine digital currencies without your knowledge or consent.
While cryptojacking is most commonly connected with websites, it may also be done using mobile apps. For example, in an incident involving the popular game Fortnite, a cryptojacking script was introduced. To avoid getting duped by a cryptojacking program, you should:
1️⃣ Check the app’s permissions request. For example, an app that wants to mine cryptocurrencies will most certainly want access to your device’s CPU and GPU.
2️⃣ Check for overheating on your mobile device, as mining requires a lot of power.
3️⃣ Install a mobile antivirus to identify malware.
▪️ Clipper Apps: The next type of malicious mobile app crypto scam is clipper apps. Clipper programs are intended to replace your cryptocurrency wallet address with the attacker’s address. For example, if you copy and paste your Bitcoin address to send some BTC to a buddy, the Clipper program will replace it with the attacker’s address.
To avoid getting defrauded by clipper applications, double-check the address to which you are sending your cryptocurrencies and install a mobile antivirus to identify malware.
▪️ Sim Swapping Apps: SIM swapping is a form of attack in which an attacker tricks your mobile service provider into moving your phone number to a SIM card under their control. Once the attacker obtains your phone number, they can use it to reset your passwords and gain access to your online accounts.
While SIM-swapping hacks are not unique to the cryptocurrency field, criminals have exploited them to obtain access to individuals’ cryptocurrency wallets and exchange accounts. To avoid getting duped by a SIM-swapping app, you should:
1️⃣ Use two-factor authentication (2FA) whenever possible. However, you should avoid utilizing a mobile phone for two-factor authentication. Instead, you should use tools like Google Authenticator, which are safer.
2️⃣ Avoid publishing your phone number on social media, since fraudsters may use the information to impersonate you and steal your cryptocurrency.
3️⃣ Be aware of any unusual behavior on your mobile device, such as unexpected text messages or phone calls.
▪️ WiFi Breaches: WiFi breaches, while not unique to the crypto world, are something to be cautious of. A WiFi breach occurs when a criminal gains access to your WiFi network and utilizes it to spy on your traffic.
If you’re using a public WiFi network, you should be especially wary of this because thieves could use it to intercept any cryptocurrency transactions you make. To avoid becoming duped by a WiFi breach, you should:
1️⃣ Avoid using public WiFi networks to conduct cryptocurrency transactions. Furthermore, if you have a large amount of cryptocurrencies stored in your mobile phone wallets, you should avoid connecting to risky WiFi networks.
2️⃣ Use a virtual private network (VPN) wherever possible to encrypt your traffic and make it harder for criminals to intercept your data.
3️⃣ Be wary of any unusual activity on your networks, such as new devices or traffic.
Conclusion
As you may have seen, each scam has its own distinct quirk or characteristic, but they all have the same purpose and operate in similar ways. New sorts of crypto scams occur on a daily basis, so be prepared. However, normal safety practices do not alter very often.
Make sure you’re aware of the information on your phone, and who you’re sharing it with (directly or indirectly), and avoid any apps or websites that you’re not certain are legitimate. To learn more about how to protect yourself from rising crypto scams, visit SunCrypto Academy.
Disclaimer: Crypto products and NFTs are unregulated and can be highly risky. There may be no regulatory recourse for any loss from such transactions. All content provided is for informational purposes only, and shall not be relied upon as financial/investment advice. Opinions shared, if any, are only shared for information and education purposes. Although the best efforts have been made to ensure all information is accurate and up to date, occasionally unintended errors or misprints may occur. We recommend you do your own research or consult an expert before making any investment decision. You may write to us at [email protected].