Blockchain technology has revolutionized the way we think about digital transactions and data storage. It is a decentralized and immutable database that is secured by cryptography. However, one of the most important concepts of blockchain technology is hashing (Hashing Strengthens Blockchain Security).
Hashing plays a critical role in the security and integrity of blockchain by providing a unique digital fingerprint of the input data, ensuring that transactions are secure and tamper-proof.
In this blog, we’ll explore what role hashing play in the blockchain network and its various applications in the world of cryptocurrencies. We will also examine the properties of cryptographic hash functions and how they are designed to meet specific security requirements.
Additionally, we will also discuss the different ways in which hashing is used in the world of cryptocurrencies, including mining, digital signatures, and wallet addresses. So, let’s dive deep into the topic.
Hashing Strengthens Blockchain Security: An In-Depth Look at Hashing!
Hashing is a fundamental concept in computer science and cryptography. It refers to the process of taking data of any size and converting it into a fixed-length output string. This output string is known as a hash. The hash is a unique digital fingerprint of the input data, and it is used to verify the integrity of the data.
Hashing is a one-way function, which means that it is impossible to retrieve the original data from the hash. This is because the process of hashing involves mapping the input data to a fixed-size output string using a mathematical algorithm. This algorithm is designed to produce a unique output for each input, which makes it difficult to reverse the process.
One of the key advantages of hashing is that it enables large amounts of data to be stored and verified using a small fixed-size string. For example, instead of storing the entire contents of a file, a hash can be calculated and stored instead. This reduces the amount of data that needs to be stored, making it more efficient and practical.
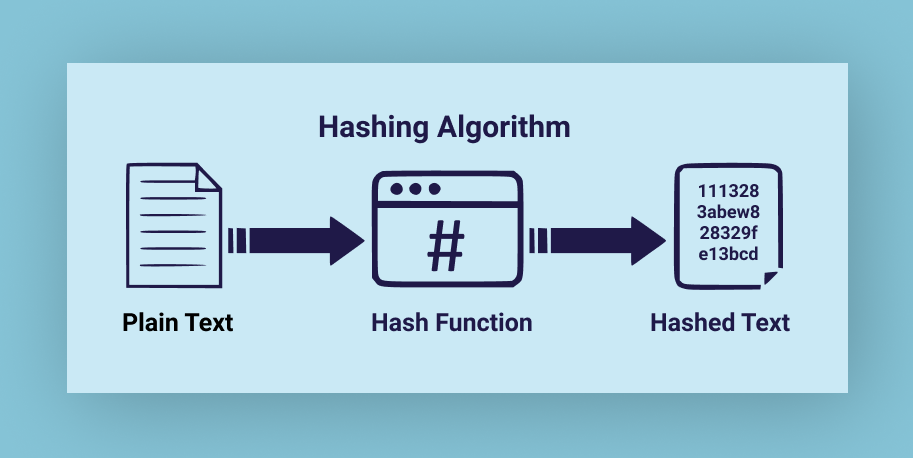
Another advantage of hashing is that it enables data to be verified quickly and securely. By comparing the hash of the data to a known value, it is possible to determine whether the data has been tampered with or modified in any way. This makes it a useful tool for verifying the integrity of digital transactions and data storage. That’s why it is such an important concept in blockchain technology.
The Secret Sauce of Blockchain: Understanding the Role of Hashing
In blockchain technology, each block in the chain contains a collection of data. This data includes transaction details, timestamps, and the hash of the previous block in the chain. The hash of the previous block serves as a unique identifier for the block. It ensures that each block is linked to the previous block in the chain.
When a new block is added to the chain, its hash is created by combining the data in the block with the hash of the previous block in the chain. This creates a chain of blocks where each block’s hash is dependent on the previous block’s hash. This makes it impossible to modify any block without changing the entire chain’s hash.
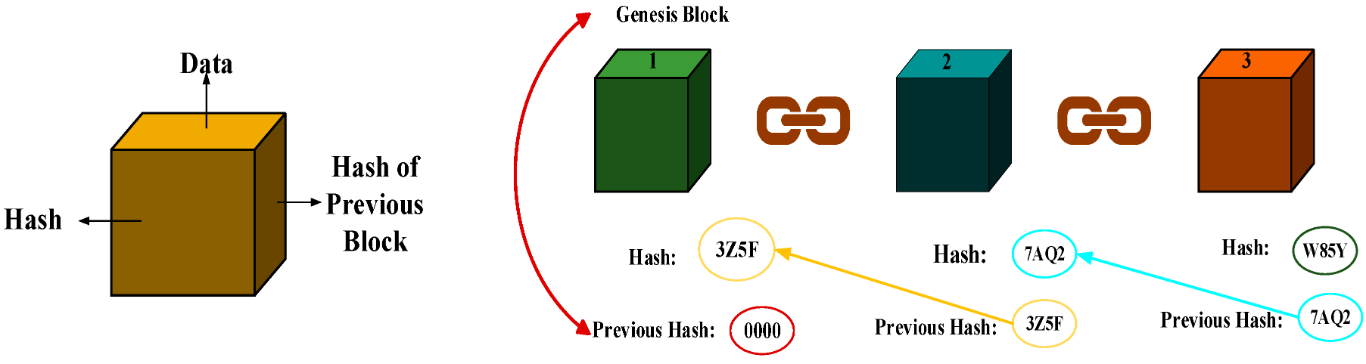
Apart from that, the hashing process in blockchain involves the use of a cryptographic hash function. That involves a mathematical algorithm that takes an input and produces a fixed-size output (the hash). The most commonly used hash functions in blockchain technology are SHA-256 and SHA-3.
This property is what gives blockchain technology its immutability and security, as any attempt to modify a block in the chain would require changing the hash of every subsequent block in the chain, which is computationally infeasible.
Furthermore, the use of hashing in blockchain technology also enables the creation of a unique digital fingerprint for each block. This allows for quick and efficient verification of the integrity and authenticity of the data stored on the blockchain.
Hashing & Cryptocurrency
In cryptocurrencies, hashing plays a critical role in ensuring the security and integrity of the blockchain. However, hashing is also used in cryptocurrencies to create a digital signature for each transaction. When a user initiates a transaction on the blockchain, the transaction details are hashed using a cryptographic hash function. The resulting hash is then signed with the sender’s private key, creating a unique digital signature for the transaction.
This digital signature serves several purposes. First, it ensures that only the sender can initiate the transaction, as only they have access to the private key needed to sign the hash. Second, it provides a way to verify the authenticity of the transaction. As the digital signature can be used to prove that the transaction was indeed initiated by the sender and has not been tampered with.
Furthermore, hashing is also used in cryptocurrencies to create the proof-of-work algorithm that underlies many popular cryptocurrencies such as Bitcoin. In a PoW system, miners compete to solve a complex mathematical puzzle, with the first miner to solve the puzzle receiving a reward in the form of a new cryptocurrency.
The puzzle that miners are trying to solve involves hashing a block of transaction data using a specific algorithm (such as SHA-256). The miner must find a hash that meets certain criteria, which requires a significant amount of computational power.
Once a miner solves the puzzle and finds a valid hash. They can broadcast the new block to the rest of the network. And the process of verifying and adding the new block to the chain begins. This ensures the integrity and security of the blockchain and makes it virtually impossible for any single entity to control the network.
Exploring the Hidden Powers of Cryptographic Hash Functions
A cryptographic hash function is a mathematical algorithm that takes an input (such as a message or data) and produces a fixed-size output (the hash or message digest). The output has several important properties that make it useful in cryptography and other applications:
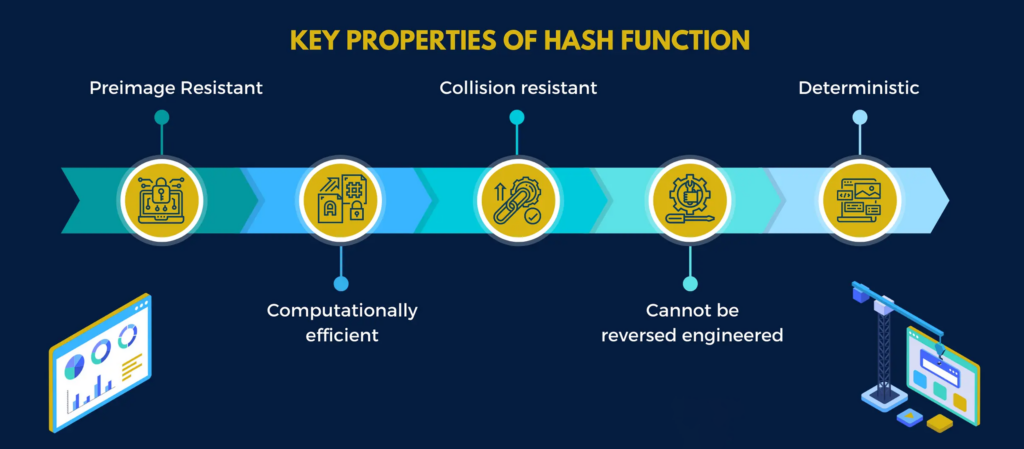
- Determinism: A hash function must always produce the same output for a given input. This property is important in cryptography because it allows for the verification of the integrity and authenticity of a message or data.
- Collision Resistance: A hash function should be computationally infeasible to find two inputs that produce the same output. This property is important in cryptography because it prevents an attacker from modifying a message without changing the hash. Since any change in the input would result in a different hash.
- Output Uniformity: The output of a hash function should appear to be uniformly random. That means each bit in the output should be independent of the other bits. This property is important in cryptography because it ensures that an attacker cannot use knowledge of the output to deduce any information about the input.
- Efficient Computation: A hash function should be computationally efficient to compute, meaning that it should be possible to compute the hash quickly and efficiently for large inputs. This property is important in many applications, such as digital signatures and cryptocurrencies, where the hash function is used frequently.
These properties ensure that a cryptographic hash function is secure and can be used in various applications. However, it is important to note that cryptographic hash functions can be vulnerable to certain types of attacks. So, it is important to use them correctly and in combination with other cryptographic tools to ensure maximum security.
Conclusion
Hashing is a fundamental concept in blockchain technology. It provides critical security features for the immutability and integrity of the blockchain. In addition, cryptographic hash functions ensure that each block in the blockchain is uniquely linked to the previous block. And the properties of the hash function make it difficult for attackers to modify or tamper with the blockchain.
As blockchain technology continues to evolve and gain widespread adoption. Hashing will remain an essential tool for securing and maintaining the integrity of decentralized systems.
To know more about how Hashing Strengthens Blockchain Security, go check out SunCrypto Academy.