A phishing attack is a fatal practice in which fraudulent actors pretend to be trustworthy sources in order to trick users into disclosing sensitive information. In this post, we’ll explain what a phishing attack is, how it works, and how to prevent falling victim to such schemes.
Crypto Phishing Scams
Phishing attack is primarily based on social engineering, a technique in which attackers influence people into disclosing personal information. Attackers gather personal information from public sources (such as social media) to create convincing emails. Victims frequently get fraudulent messages that appear to come from familiar connections or respectable organizations.
The most common type of phishing is through emails that contain malicious links or attachments. Clicking on these links may install malware on the user’s device or direct them to fraudulent websites that steal personal and financial information.
While it is easy to identify poorly written phishing emails, fraudsters are using modern tools such as chatbots and AI speech generators to improve the legitimacy of their attacks. This makes it difficult for users to discern between legitimate and fraudulent communications.
How to Recognize a Phishing Attack?
Identifying phishing emails can be challenging, but there are certain indicators you can keep an eye out for.
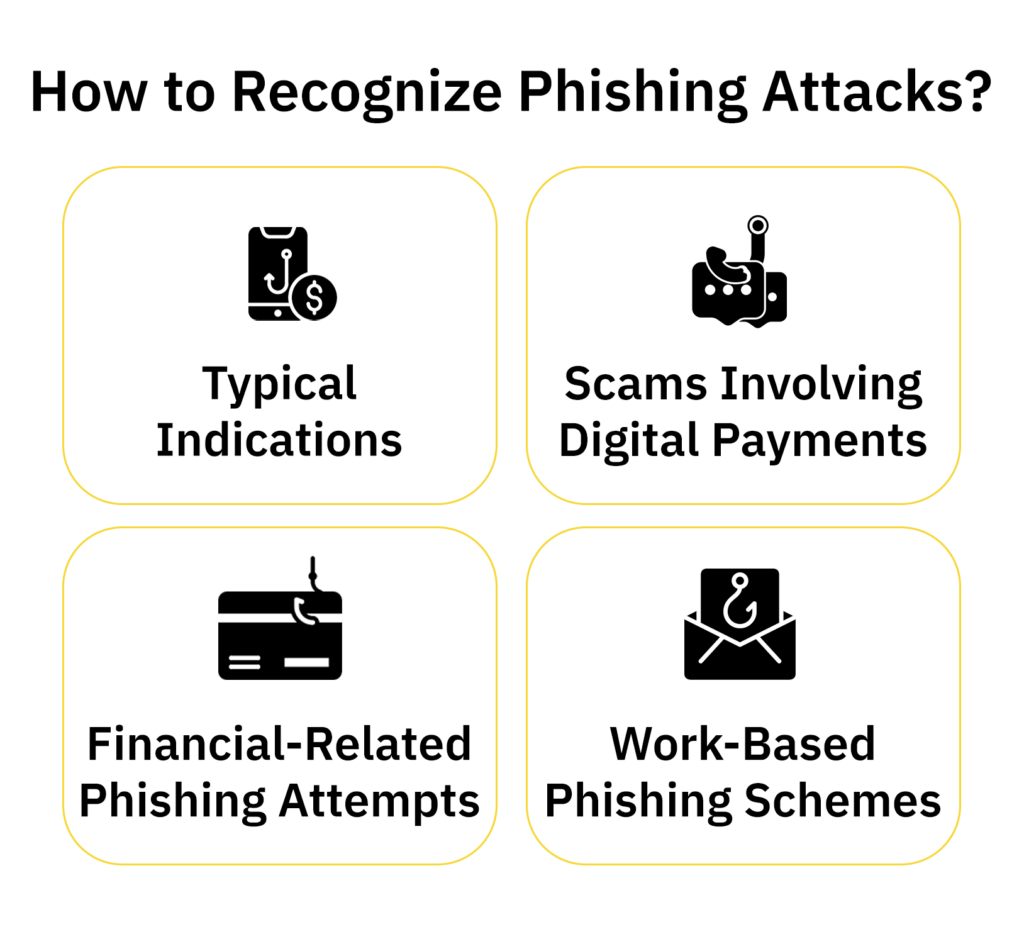
▪️ Typical Indications: Exercise caution if the email includes suspicious links, employs generic email addresses, instills a sense of fear or urgency, asks for personal details, or contains spelling and grammar mistakes. It’s often possible to inspect the URLs by hovering your cursor over them without clicking.
▪️ Scams Involving Digital Payments: Fraudsters frequently impersonate reputable online payment services such as PayPal, Venmo, or Wise. They send out deceptive emails prompting recipients to verify their login credentials. It’s essential to stay alert and promptly report any dubious activity.
▪️ Financial-Related Phishing Attempts: Con artists masquerade as banks or financial entities, alleging security breaches in order to obtain sensitive information. They commonly use deceptive emails regarding money transfers or schemes targeting new employees with false direct deposit claims, sometimes urging immediate action for a purported security update.
▪️ Work-Based Phishing Schemes: These targeted scams involve attackers posing as high-ranking executives, like CEOs or CFOs, and soliciting wire transfers or fictitious purchases. Another tactic employed by scammers is a voice phishing attack, which utilizes AI voice generators during phone calls.
How to Protect Yourself from a Phishing Attack?
To avoid phishing attempts, it is crucial to use numerous security measures. Avoid clicking on links immediately. Instead, visit the company’s official website or communication channels to confirm that the information you received is accurate. Consider utilizing security measures like antivirus software, firewalls, and spam filters.
In addition, organizations should employ email authentication standards to validate inbound emails. Email authentication solutions include DKIM (DomainKeys Identified Mail) and DMARC (Domain-based Message Authentication, Reporting, and Conformance).
Individuals should inform their family and friends about the dangers of a phishing attack. Companies must educate personnel about phishing strategies and conduct frequent awareness training to reduce risks.
If you require additional support and information, check out government efforts like OnGuardOnline.gov and organizations like the Anti-Phishing Working Group Inc. They offer more in-depth tools and guidance on detecting, avoiding, and reporting phishing assaults.
Types Of Phishing Attack
Phishing attack techniques continue to evolve, as cybercriminals employ a variety of methods to deceive individuals. These methods can be categorized based on the target and the method of attack. Let’s delve into the different types:
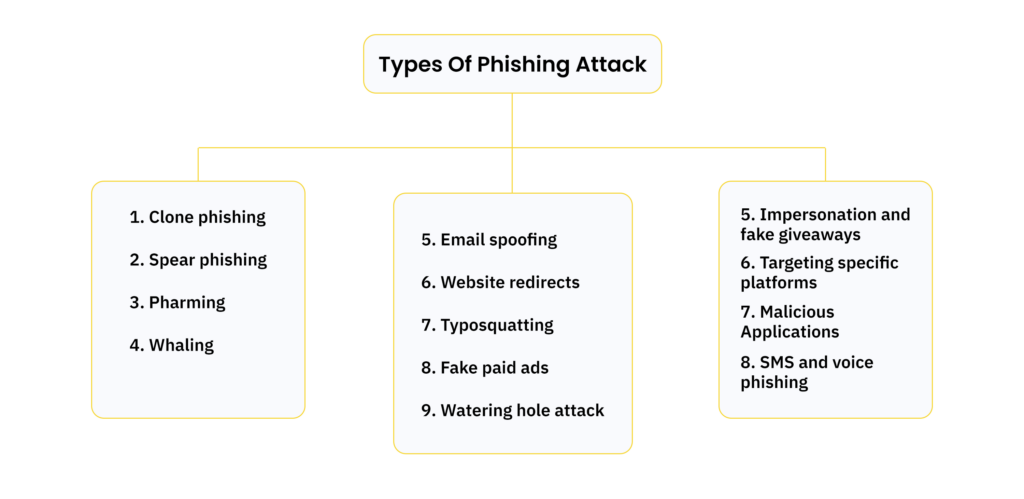
▪️ Clone phishing: Here, attackers replicate legitimate emails, altering them slightly to include links to malicious websites. They may claim the link is updated or new, tricking recipients into visiting harmful sites.
▪️ Spear phishing: This targeted approach involves gathering specific information about an individual or organization to craft personalized attacks. By using details like the victim’s contacts or preferences, cybercriminals aim to lure them into interacting with malicious content.
▪️ Pharming: Attackers manipulate DNS records to redirect users from legitimate websites to fraudulent ones they control. This tactic is particularly dangerous as users have little control over DNS settings.
▪️ Whaling: Similar to spear phishing but targeting high-profile individuals such as CEOs or government officials.
▪️ Email spoofing: Phishing emails mimic legitimate communications, often leading recipients to fake login pages where personal information is stolen through various malicious scripts.
▪️ Website redirects: Exploiting vulnerabilities, attackers redirect users to unintended URLs and may install malware on their devices.
▪️ Typosquatting: Redirecting traffic to counterfeit websites through domain names that resemble legitimate ones, exploiting common misspellings or variations.
▪️ Fake paid ads: Using paid advertisements to promote counterfeit websites, often appearing as top search results on search engines.
▪️ Watering hole attack: Attackers identify frequently visited websites by users and inject malicious scripts to target them when revisiting these sites.
▪️ Impersonation and fake giveaways: Phishers impersonate influential figures, engaging in deceptive practices like fake giveaways or promotions, often via social media.
▪️ Targeting specific platforms: Recent trends show increased phishing activity on platforms like Discord, X, and Telegram, where attackers spoof chats, impersonate individuals, and mimic legitimate services.
▪️ Malicious Applications: Phishers may distribute malicious apps disguised as legitimate tools, which monitor user behavior or steal sensitive information, particularly targeting cryptocurrency users.
▪️ SMS and voice phishing attack: Using text messages or voice calls, cybercriminals attempt to extract personal information from users through deceptive tactics.
Phishing Attack in Blockchain & Crypto Space
While blockchain technology’s decentralized structure ensures high data security, users in the blockchain space should be wary of social engineering and phishing attacks. Cybercriminals frequently use human vulnerabilities to get access to private keys or login credentials. Most frauds are based on human error.
Scammers may also attempt to mislead users into disclosing their seed words or transferring money to fraudulent addresses. It’s critical to be cautious and follow security best practices.
Conclusion
Understanding phishing attacks and staying up-to-date on emerging strategies is critical for protecting personal and financial information. Individuals and organizations may protect themselves from the ever-present threat of phishing in our interconnected digital world by combining strong security measures, education, and awareness.
To learn more about the ways to prevent a phishing attack, visit SunCrypto Academy.
Disclaimer: In addition, Crypto products and NFTs are unregulated and can be highly risky. There may be no regulatory recourse for any loss from such transactions. All content provided is for informational purposes only, and shall not be relied upon as financial/investment advice. Opinions shared, if any, are only shared for information and education purposes. Although the best efforts have been made to ensure all information is accurate and up to date, occasionally unintended errors or misprints may occur. We recommend you do your own research or consult an expert before making any investment decision. You may write to us at [email protected].